Decrypting iOS applications - iOS 12 Edition
As some of you may know, with the release of iOS 12.4 Apple accidentally reintroduced a vulnerability already patched on iOS 12.3. Shortly after this discovery, @Pwn20wnd released a new version of Unc0ver that supported iOS 12.4. This meant that many users were able to update to the latest version of iOS and jailbreak it. (In fact at the time of this writing it's still possible to update to iOS 12.4).
To keep up with the new version of iOS, I'm writing this post to update my previous post on the matter. With the exception of the decryption process, the rest of the steps are the same, which is why I'll focus only on the decryption step.
Jailbreak your device (<= A11)
- Download the latest version of Unc0ver.
- Download (if you haven't already) Cydia Impactor.
- Connect your iPhone to your computer.
- Drag & Drop the Unc0ver IPA on Cydia Impactor.
- Enter your developer credentials.
- Trust the the developer certificate for this app by:
- Open the Settings.app
- Navigate to General -> Profiles & Device Management
- Tap on your developer account
- Tap on Trust. - Disable Siri by disabling the top 3 options from Siri & Search.
- Put your device on Airplane Mode.
- Restart your device.
- Launch Unc0ver.
- Tap the Settings gear and enable 'Reinstall Cydia'.
- Tap on Jailbreak.
- It may reboot a couple of times, just relaunch Unc0ver and tap Re-Jailbreak.
- You're done!
Decrypt an iOS app using frida-ios-dump
- Launch Cydia and install Frida.
- Clone or download frida-ios-dump from its GitHub repo.
- Install the dependencies
sudo pip install -r requirements.txt --upgrade. - Forward SSH connections over USB with iTunnel/usbmuxd.
- Edit
dump.pyto match your device's settings like root password (default isalpine) and SSH forwarding port. - Run
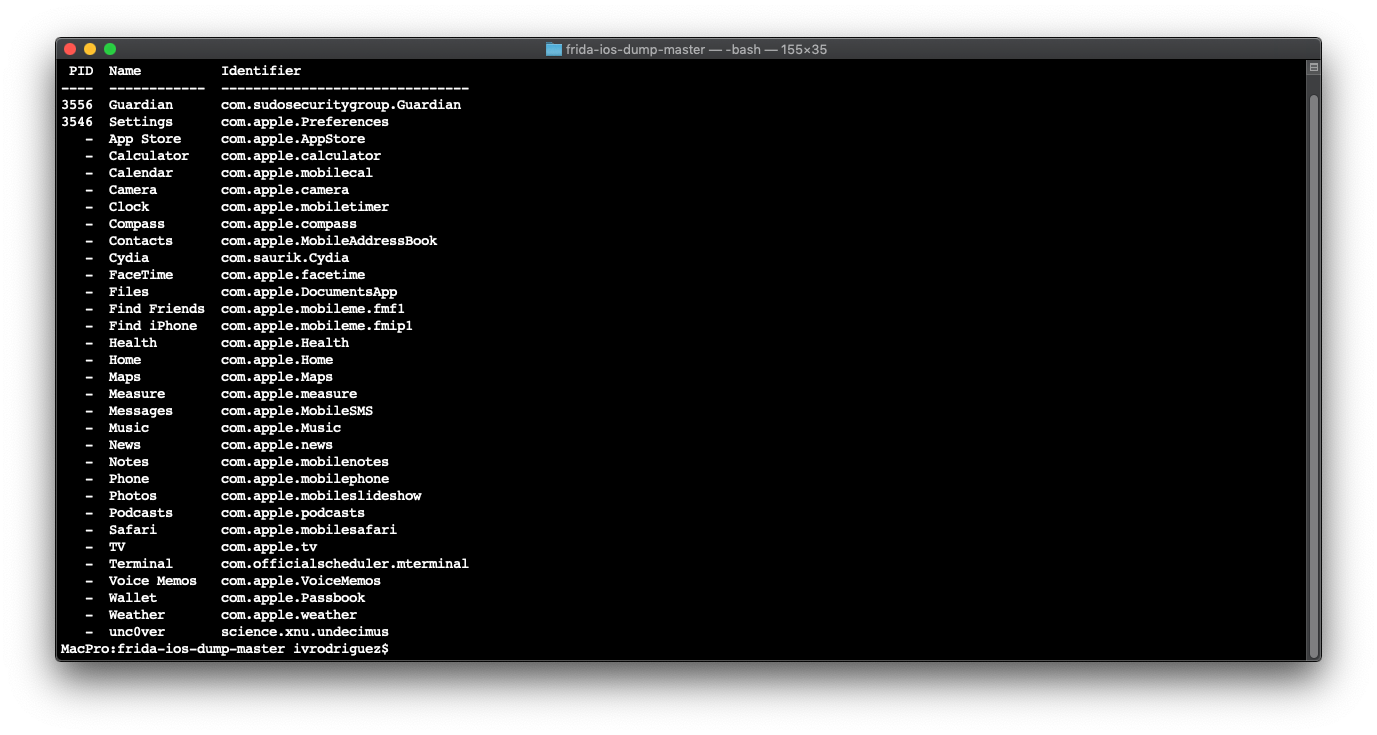
./dump.py -lto list the installed applications. - Copy the app's
Identifier. - Run
./dump.py <identifier>to decrypt the app. - You'll see the app being launched and then, if all goes well, you should have a
.ipabundle on the same directory where you ran the script. - That's it!
Conclusions
- I didn't use
BFInjectbecause I was having trouble getting it to work on iOS 12 and haven't had any spare time to investigate further. - With this unintentional gift from Apple, you can now have the latest version of iOS jailbroken on your device and combined with this fantastic script from AloneMonkey you can start decrypting and researching on iOS applications on iOS 12.
- One of the best benefits of this method is that there's no need to SSH into the device and run
Clutch,dumpdecryptedorBFInject. The script is ran from your Mac and the decrypted version is transferred from your phone to your current directory.
As always, if you see an error or have any questions, please reach out @ivRodriguezCA.
Happy decrypting!
